![]() Nowadays, people frequently need to connect themselves remotely on a computer network to monitor an installation or perform maintenance tasks. However, because of computer attacks which any machine connected to the Internet faces, we usually lock all possible doors, except one that we consider safe. For example, we only keep one secure VPN gateway. But if the gateway fails, it's a disaster... So, how can you avoid finding yourself without access to your network, but without opening an additional door?
Nowadays, people frequently need to connect themselves remotely on a computer network to monitor an installation or perform maintenance tasks. However, because of computer attacks which any machine connected to the Internet faces, we usually lock all possible doors, except one that we consider safe. For example, we only keep one secure VPN gateway. But if the gateway fails, it's a disaster... So, how can you avoid finding yourself without access to your network, but without opening an additional door?
It's a relatively simple issue:
- We want a mechanism enabling us to restore a VPN gateway remotely.
- We don't want, while doing so, to open another entry door on the secure network .
Usually, restarting the VPN gateway (or any other network device) is enough to restore it to working order. Therefore, we need a way to do so automatically, and only when we need it. That's where Yoctopuce modules are useful and we are presenting two rather different solutions to solve this issue.
First solution: the watchdog on the power supply
A watchdog is an autonomous countdown able to force a hardware restart, usually by shutting off the power supply. Normally, the countdown is automatically reset before the restart happens but, in case of important network failure (or on demand), the watchdog can deactivate the 12V power supply of the VPN gateway for a few seconds in order for it to restart properly.
Here is the installation diagram:
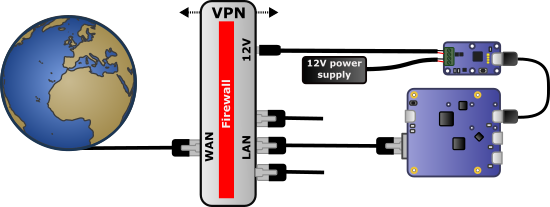
A watchdog on the VPN gateway power supply
We put a Yocto-WatchdogDC on the power wire of the VPN gateway, driven through a YoctoHub-Ethernet protected behind the firewall.
Normally, the YoctoHub-Ethernet performs an HTTP callback (outgoing connection) every 15 minutes to a web server where a short PHP script resets the watchdog counter:
include("yocto_watchdog.php");
yRegisterHub("callback");
$watchdog = yFirstWatchdog();
if($watchdog) {
$watchdog->reset();
}
The watchdog itself is configured with a 2 hour countdown for example. Thus, if the network fails during 2 hours, no HTTP callback runs to reset the counter and the gateway is automatically restarted.
Sometimes, the outgoing network works fine, only the VPN access fails. In this case, we can also manually trigger a gateway restart, through the PHP script which will run at the next callback, within the next 15 minutes. The callback should then simply trigger a 10 second pulse on the watchdog:
Second solution: restarting through the serial console
When possible, it's best to avoid brutally restarting a gateway by shutting off the power supply: in most cases, there is a kernel with a file system within the VPN gateway. By shutting off the power, this file system risks to be corrupted in the long run.
A more elegant way to force a restart (still assuming that your only entry access point is a VPN which doesn't work anymore) consists in using the RS232 console port, which is available in most of these devices. Naturally, a serial console is designed for local use but, thanks to the Yocto-RS232, you can use the HTTP callback trick again to send commands on the the RS232 console:
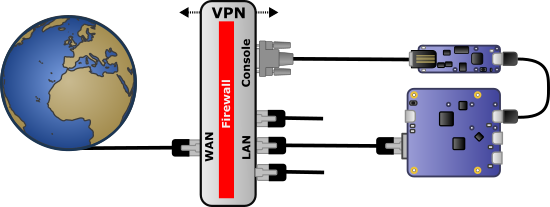
Serial console and HTTP callback
An HTTP callback doesn't allow full interaction with the console, but it allows you however to very easily run a predefined task on the Yocto-RS232:
{
$serialport = yFirstSerialPort();
if($serialport) {
$serialport->selectJob("rebootZywall.job");
}
}
By defining for example a task like illustrated below, you can easily trigger a "clean" restart of the VP gateway:
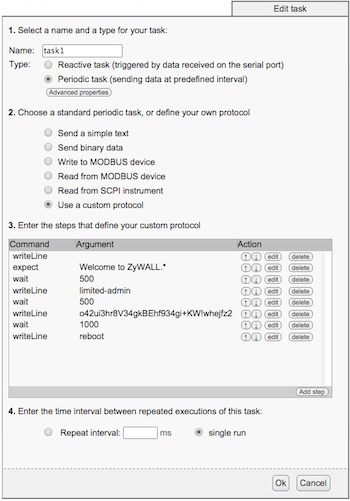
Job defined on the Yocto-RS232
By the way, note that this solution is much more secure than one consisting in opening an access to the console directly on Internet: not only you avoid attacks by not opening any port but, on top of it, the password enabling access to the gateway console is confined inside the secure space as it is stored directly in the job file, in the Yocto-Serial flash memory.


