 We are constantly improving our products, our programming libraries, as well as our tools. This week, we are writing about a new feature that we just added to the VirtualHub: the HTTPS support. We even offer you to test this new feature by using the beta version of the VirtualHub 2.0.
We are constantly improving our products, our programming libraries, as well as our tools. This week, we are writing about a new feature that we just added to the VirtualHub: the HTTPS support. We even offer you to test this new feature by using the beta version of the VirtualHub 2.0.
Currently, communications between our modules and the applications using them are not encrypted. Communications are secured with an authentication and a password (we have, by the way, a post on this topic), but the sensor data are not encrypted. Theoretically, if someone has access to your network, that person can spy the content of the transactions with the exception of the password. In practice, this kind of attack is complex to set up and of little interest. But the absence of HTTPS support is also penalizing for other uses. For example, the VirtualHub and the YoctoHubs cannot connect to some cloud services because the latter accept only HTTPS connections.
For these reasons, we decided to add HTTPS support to our whole architecture. This feature is going to be gradually added to the different parts of our ecosystem. And the first step is the VirtualHub.
VirtualHub 2.0
Despite the major version change, the new VirtualHub 2.0 remains compatible with all the Yoctopuce components. As usual, we took care not to break backward compatibility. Actually, from the outside, version 2.0 is identical to version 1.0, but internally we wrote a large portion of the code over.
The main new feature is the addition of SSL/TLS support enabling the VirtualHub to accept incoming HTTPS connections. From now on, the VirtualHub accepts classic HTTP connections on port 4444 and HTTPS connections on port 4443. You can access the VirtualHub in a secure and encrypted way with your browser with the https://myhostname:4443 URL.
Naturally, you can configure these ports with options passed on the command line:
- option -p enables you to change the HTTP port
- option -P enables you to change the HTTPS port
- option --no_https completely disables SSL/TLS support
- option --only_https forces the use of HTTPS connections for all incoming connections
Note that to accept incoming HTTPS connections, the VirtualHub needs an SSL certificate in the CSR format and a private key. By default, it looks for the .virtualHub.csr and .virtualHub.key files in the directory of the configuration file. You can change the path of these two files with the -s and -k options.
Note: This step is no longer necessary. The VirtualHub automatically generates a self-signed certificate during the first start.
We don't provide a private key certificate with the VirtualHub. If you don't have a certificate, you can create these two files with the following command:
openssl req -newkey rsa:2048 -nodes -x509 -days 365 -keyout .virtualhub.key -out .virtualhub.crt
Outgoing callbacks
We also added SSL/TLS support for outgoing connections. Form now on, you can configure an outgoing callback on a server requiring an HTTPS connection. This enables you, for example, to have a secure and encrypted connection between the VirtualHub and the PHP library.
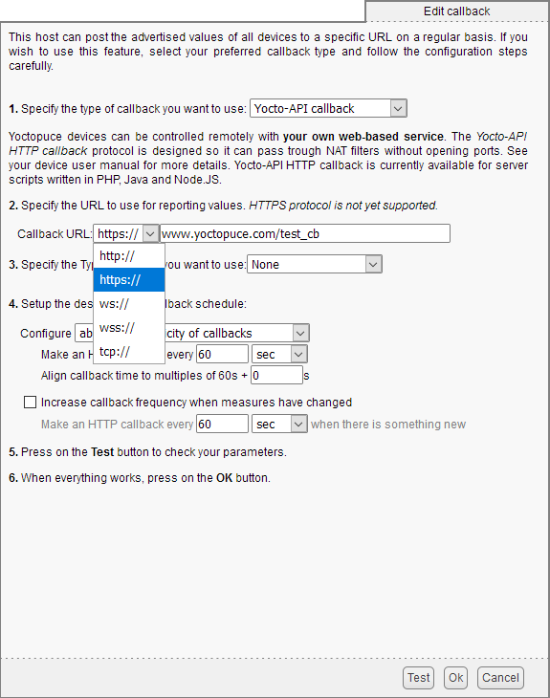
You can now configure a callback on a web server which accepts HTTPS connections
From now own, the VirtualHub can connect itself to Cloud services which accept only HTTPS connections, such as for example InfluxDB OSS v2.0.
Testing the beta version
This new version of the VirtualHub is still very young and, for sure, it is not bug free yet. We nevertheless decided to publish it in beta version so that you can already test it. Currently, we only support the following architectures:
- Windows Intel 32 and 64 bits
- Linux Intel 32 and 64 bits
- Linux ARM 64 bits
macOS Intel and Apple Silicone versions should follow very soon.
You can download version 2.0 binaries from the VirtualHub page.
If you find bugs or if you have suggestions, don't hesitate to pass them on to support (support@Yoctopuce.com).
Still to be done...
As said above, this is the first step for the migration towards SSL/TLS encryption of the communications. Support for the encryption of communications in the programming libraries is in the pipeline and should come out in the near future.
The last step is SSL/TLS support in the YoctoHubs. Unfortunately, the CPUs which are used in the YoctoHubs are not powerful enough for this feature. However, we are working on the issue and we should reach a solution in 2021.


