 We've received a few messages from customers who were surprised the first time they used VirtualHub v2 (still in beta). Indeed, the first time you connect to the VirtualHub v2 web interface, the browser blocks the page and displays a big warning about an invalid certificate. But don't panic! It's nothing serious. We'll explain everything.
We've received a few messages from customers who were surprised the first time they used VirtualHub v2 (still in beta). Indeed, the first time you connect to the VirtualHub v2 web interface, the browser blocks the page and displays a big warning about an invalid certificate. But don't panic! It's nothing serious. We'll explain everything.
VirtualHub v2 uses secure SSL/TLS connections. SSL/TLS authentication is based on a chain of digital certificates. When the connection is established, the client checks the validity of the certificate chain, ensuring that at least one of the certificates in the chain has been issued by an authority recognized by the client. To establish a 100% secure connection, the client - in this case, the browser - needs to know the certificate issuers of the server to which it is trying to connect.
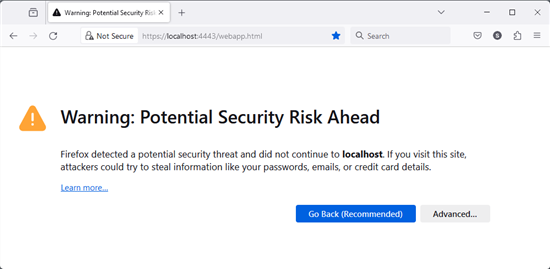
On first connection, the browser does not know the certificate
What is an SSL certificate?
A certificate is a small cryptographic data file that binds a cryptographic key to server details. This includes the URL of the server, the name of the entity that issued the certificate, and the certificate's validity date.
A certificate is a kind of passport for a server. When connecting, the client requests the server's passport and checks that it corresponds to what the client expects. It checks that the certificate is still valid, and that the URL for which the certificate is intended is the one the client is using. Finally, it checks that the entity that produced the certificate is a trusted entity.
There are two types of certificate: self-signed certificates and official certificates.
Official certificates are issued by recognized certification authorities and involve rigorous validation of the site owner's identity. These are typically the certificates you find on every web site. These certificates have to be paid for and are only issued by universally recognized entities (Comodo, DigiCert, and so on). These certificates are automatically recognized by web browsers, since the browser knows the certification authorities.
Self-signed certificates, on the other hand, are generated by the server administrator, without the involvement of a certification authority. Consequently, these certificates are not known to the web browser.
From a cryptographic point of view, both types of certificates offer the same encryption quality and contain the same information, but official certificates are validated by a common certification authority between server and client.
Why do I get a warning with VirtualHub v2?
To accept SSL/TLl connections, VirtualHub needs an SSL certificate. On first startup, VirtualHub generates a self-signed certificate and saves it in the same directory as the configuration files.
This certificate is valid for 2 years and for the following host names:
- the host name configured by the OS
- the "localhost" host name
- the 127.0.0.1 address (IPv4)
- the ::1 address (IPv6)
But this certificate is self-signed, so your web browser can't verify its authenticity with a certification authority. This is why the web browser displays this message on the first connection.
You're probably wondering why VirtualHub doesn't come with an official certificate. Apart from the cost, it's impossible to guess your machine's host name in advance. This certificate must uniquely identify your VirtualHub installation.
What can you do?
There are two solutions:
- Add this certificate to the list of certificates recognized by the web browser
- Configure VirtualHub to use an official certificate
Adding a certificate to the browser
The first solution is very simple and corresponds to 99.9% of cases. When the web browser blocks access to the web site, click on the button to add the certificate to the list of accepted certificates.
For most browsers, this is done in 2 steps. The first is to access the "advanced" section, which displays more information on the certificate and includes a button for installing the certificate.
With Firefox, click on "Advanced" and then on "Accept the Risks and Continue".
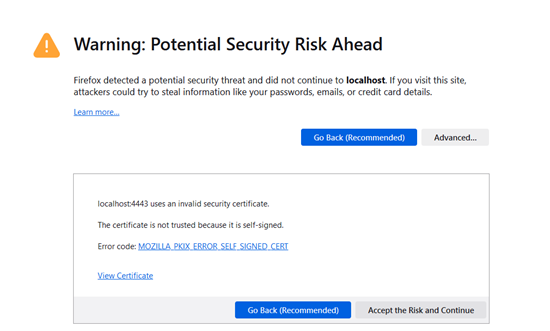
The button to add a certificate in Firefox
With Chrome and Edge, click on "Advanced...", then on the "Proceed to XXXX (unsafe)" link at the bottom of the page.
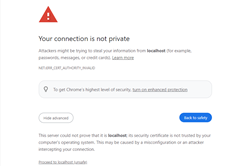
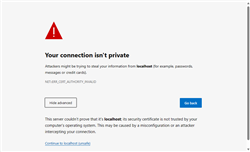
With Chrome and Edge, click on "Advanced...", then on the "Proceed to XXXX (unsafe)" link at the bottom of the page.
Once done, the browser accepts to connect to VirtualHub. This operation should only be carried out when connecting for the first time.
Using an official certificate
The second solution is to buy and use an official certificate. This solution eliminates the warning, but requires you to purchase and manage an SSL certificate in the same way as for a web site. Purchasing and managing these certificates is far more complex, and would require a dedicated post. But if you want to install your own certificate, it's possible. Simply launch VirtualHub with the -s option followed by the path of the certificate you wish to use.
Conclusion
You now know why VirtualHub v2 is not automatically recognized by your browser. It's not because it's infected by a virus, but because of the way SSL certificates work. This problem doesn't just concern VirtualHub, but any application or object connected to your network. The same "problem" is present on NAS servers or Wifi routers.


